Fake Job Recruitment Phishing Scam (Credential Harvesting & Data Theft)
Case Overview
Job phishing scams are on the rise, targeting professionals through emails that appear to come from legitimate recruiters. These scams exploit trust, urgency, and the desire for career growth to steal personal information and conduct follow-up fraud.
In this case study, we analyze a fake job recruitment email that impersonated a hiring process for an Information Security & Systems Administrator role. The goal is to highlight how the scam works, why it is effective, and how individuals and organizations can protect themselves.
The phishing email claimed to be from a recruiter who discovered the recipient’s profile via LinkedIn Sales Navigator. It advertised a remote role with a foreign company and directed the recipient to view the job description using a Google Docs link.
At first glance, the email looked reasonable. However, closer inspection revealed multiple warning signs indicating a recruitment phishing attempt.
Key Red Flags Identified
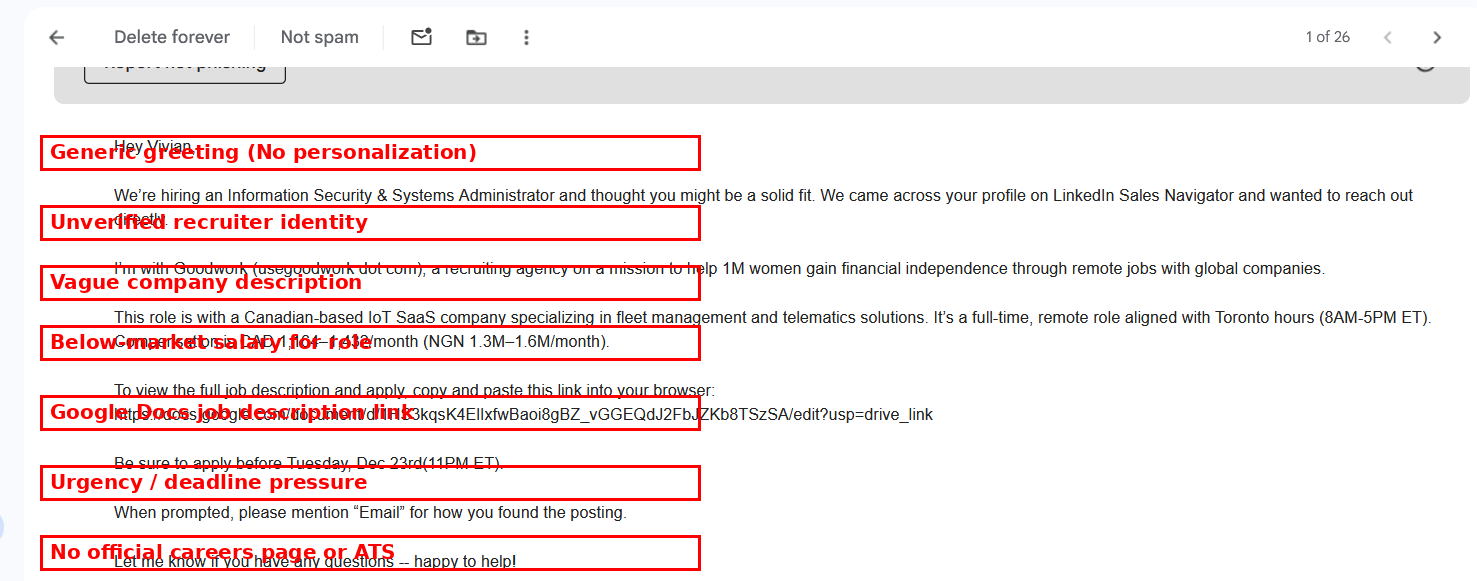
1. Generic Greeting
The email used a non-personalized greeting and did not reference the recipient’s background, current role, or company. Legitimate recruiters typically personalize their outreach.
2. Unverified Recruiter Identity
No recruiter name, LinkedIn profile, or verifiable corporate email address was provided. This makes it impossible to confirm the sender’s legitimacy.
3. Vague Company Information
The hiring company was described only as a “Canadian-based IoT SaaS company” with no name, website, or physical address. Legitimate job opportunities clearly identify the employer.
4. Use of Google Docs Instead of a Careers Page
The job description was hosted on Google Docs rather than an official company website or applicant tracking system (ATS). This is a common tactic used in phishing campaigns to bypass security controls and build false trust.
5. Artificial Urgency
The email pressured the recipient to apply before a fixed deadline. Urgency is often used to discourage verification and critical thinking.
6. No Formal Hiring Process
There was no mention of interview stages, HR contacts, or official application channels. Legitimate organizations follow structured hiring processes.
How the Scam Works
This phishing attempt is designed as a multi-stage attack:
- Initial Contact: The victim receives a believable job opportunity via email.
- Engagement: The victim clicks the Google Docs link and reviews the role.
- Data Collection: The victim is asked to submit personal details or a CV.
- Follow-Up Fraud: The attacker may conduct fake interviews, send offer letters, or request payments or sensitive documents.
The real damage often occurs after the victim engages with the initial message.
Why This Scam Is Effective
• It uses realistic job language, not obvious scam wording
• It leverages trusted platforms like Google Docs
• It targets professionals who expect recruiter outreach
• It relies on psychological pressure, not malware
This makes the scam difficult to detect using traditional security tools alone.
Security Impact
If successful, this type of scam can lead to:
• Exposure of personal and professional data
• Identity theft
• Financial fraud
• Further targeted attacks using the victim’s information
For organizations, employees falling for such scams may also expose internal details that can be used in future attacks.
How to Protect Yourself
For Individuals
• Verify recruiter identities on LinkedIn
• Avoid job applications hosted on public document platforms
• Be cautious of urgent job offers
• Never share sensitive information without confirmation
For Organizations
• Train employees on recruitment-based phishing scams
• Monitor and filter external document links
• Encourage reporting of suspicious job emails
• Promote a “verify before trust” culture
Key Takeaway
Modern phishing scams do not look suspicious, they look reasonable.
Job phishing attacks succeed by exploiting trust, expectations, and human behavior. Awareness and verification remain the strongest defenses.
Conclusion
This case study demonstrates how recruitment-themed phishing scams continue to evolve, targeting professionals with believable job offers. By understanding the tactics used and recognizing early warning signs, individuals and organizations can significantly reduce their risk.
At Nexsecure Cyber Limited, we help organizations detect, prevent, and respond to social engineering threats through awareness, monitoring, and security best practices.
